Switching devices is an expensive habit, especially considering that the best iPhones can cost over $1,000. In recent years, midrange alternatives have become much more affordable, but purchasing a used phone is another excellent way to save money.
Buying a new phone is an exciting experience, but it can rapidly turn frustrating if it is locked. A locked phone restricts its use with multiple carriers and access to certain features. If you have purchased a secured phone, we will discuss the steps you can take and the options you have in this blog.
Understanding the Situation
Prior to panicking, it is essential to comprehend what a restricted phone is. A locked phone is typically bound to a particular carrier, preventing the use of a SIM card from a different carrier. Typically, this restriction is part of a contract or payment plan. Understanding the problem is the first step in discovering a solution

Contact the Seller
If you purchased the phone from a private vender or a third-party retailer, contact them as soon as you discover it is locked. Explain the situation and ask if there was a misunderstanding or if they can assist with unlocking the phone. Occasionally, sellers are prepared to provide assistance or a refund if the problem was not disclosed prior to the sale.
Check for Carrier Unlock Options
If the phone is confined to a specific carrier, contact customer support for that carrier. In some instances, carriers may be willing to unlock your phone, particularly if you’ve fulfilled the terms of the phone’s contract or payment plan. Be prepared to provide information such as the IMEI number of the phone.
However, if you did not meet their requirements for unlocking your device, do not fret. Freeunlocks has got your back; simply follow the instructions below.
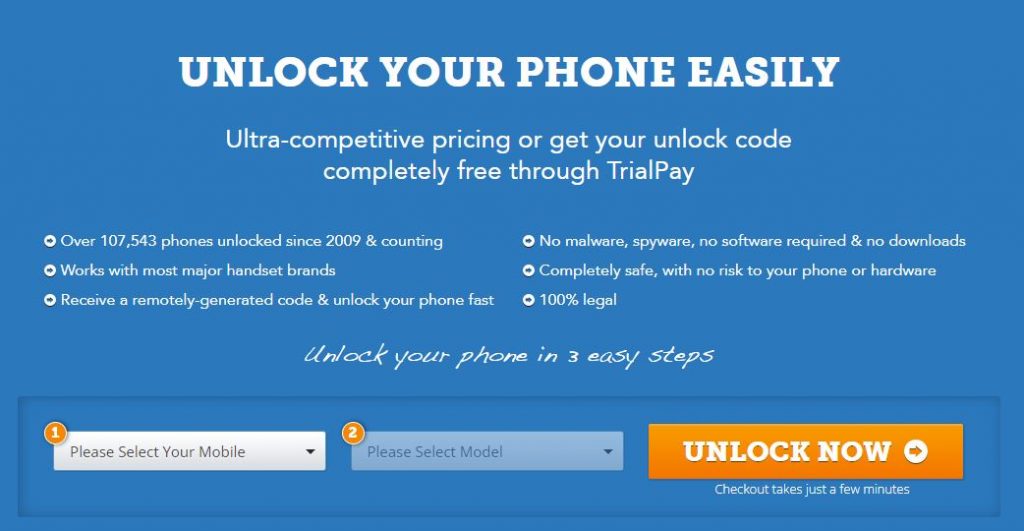
Unlocking a Used Phone
Visit the website: https://www.freeunlocks.com/
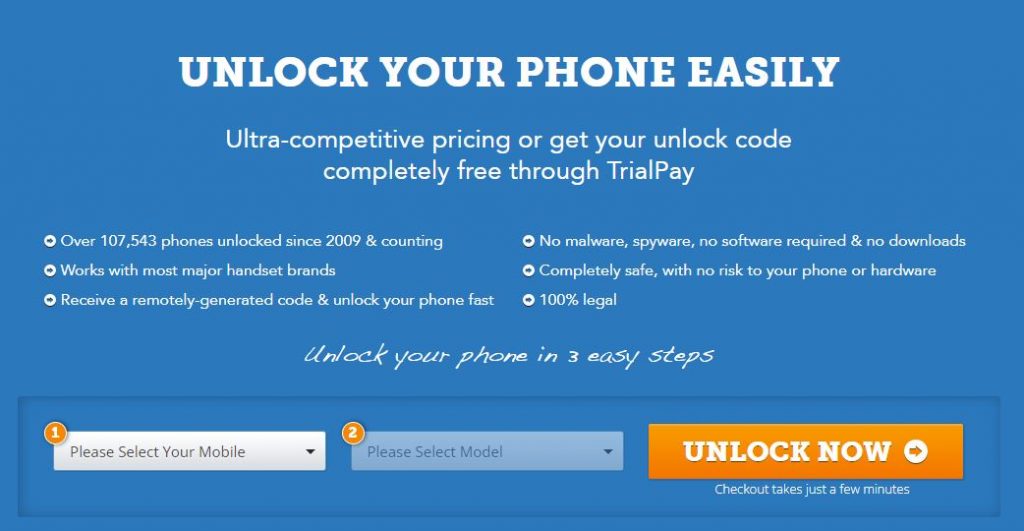
Even if you were unable to meet the requirements set forth by your carrier, Freeunlock can assist you in unlocking your phone. You need only follow the steps below:
- Select the mobile device’s manufacturer.
- Enter your phone’s IMEI number
- Type your email address
- You will be prompted to choose the country to which the phone is restricted
- Select your network or service provider.
- Confirm that your payment was processed successfully, and then await a confirmation email.
Please follow the next instructions below:
- Remove the SIM card that was included with your phone.
- Insert a SIM card from a carrier other than your current one.
- The screen should promptly display a box where you can enter the unlock code.
- Enter the unlock code that FreeUnlocks has provided you.
That concludes everything that needs to be said. Anywhere in the world, you are free to use your Used Mobile Phone with any network.

Consider Legal and Consumer Rights
In some regions, consumer protection laws require sellers to disclose whether or not a phone is locked prior to sale. If you discover that the seller intentionally withheld this information, you may be entitled to a refund or compensation under the law. Research the local laws to determine your privileges.
Conclusion
The discovery that the phone you’ve purchased is locked can be frustrating, but there are ways to rectify the situation. Taking a step-by-step approach can help you regain access to your device. Always remain informed of your consumer rights, and approach any solution with caution.
↓ Can we unlock your phone? Start here! ↓